How Strong Is Your Current Storage Defense Infrastructure?
May 13, 2025
Event Insight
As data threats intensify and breaches grow more sophisticated, storage defense infrastructure has become a frontline priority—not just a back-office concern. In our recent BeTechly event, storage security experts Adam Dean (Co-Founder, h-Bar Solutions) and Tom Walter (Sr. Account Manager, Systems Analysis Services Inc.) broke down today’s top storage challenges, common pitfalls, and the most effective strategies for protecting critical business data.
The Top Challenges Businesses Are Facing
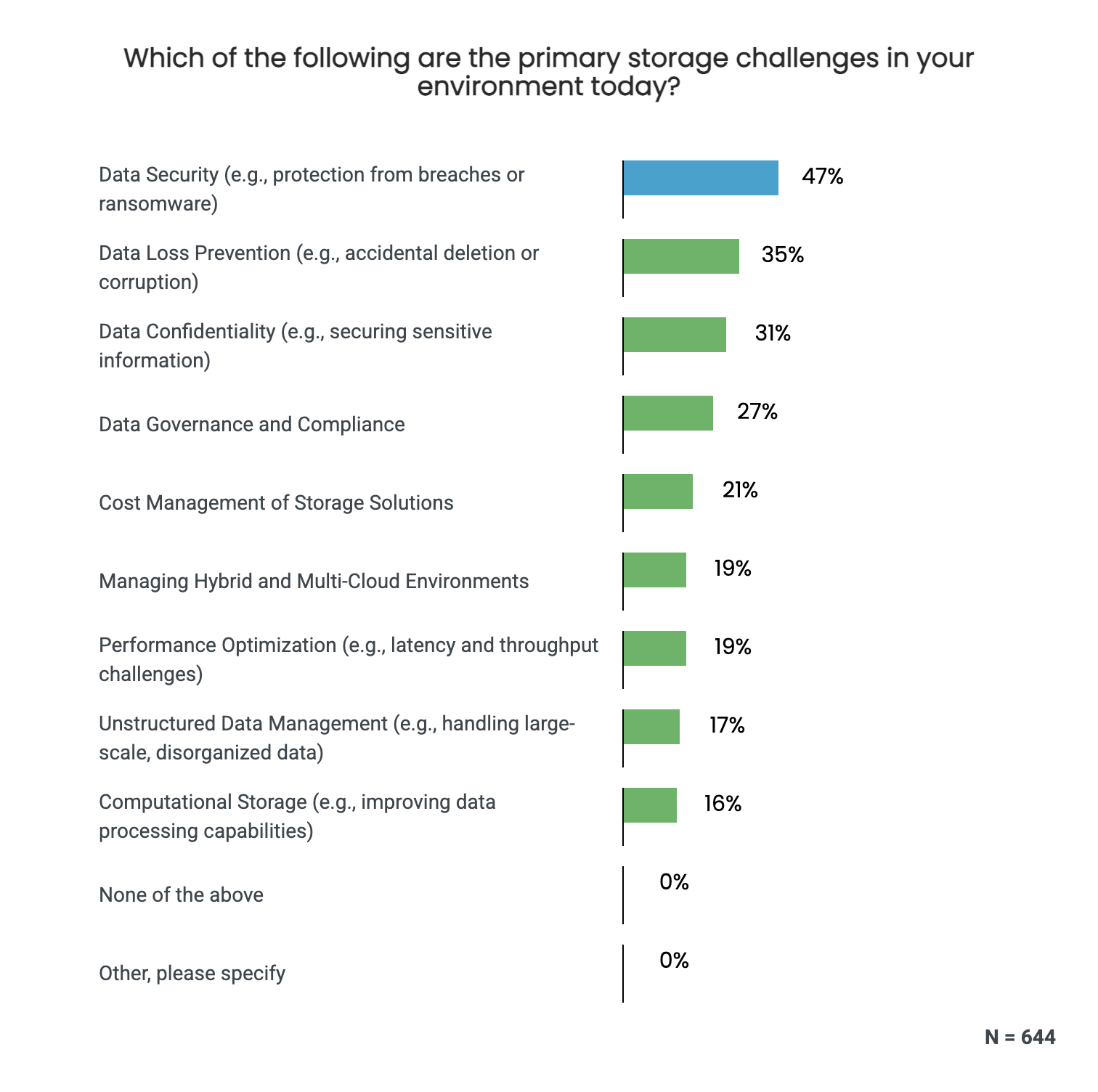
In a BeTechly survey of 644 business and technology decision-makers, respondents cited data security is their top storage challenge (47%), followed by data loss prevention (35%) and data confidentiality (31%).
Dean confirmed that these findings reflect what he sees with his own clients, highlighting the need for robust access controls, up-to-date security tools, and consistent audits. He warned that without these safeguards in place, organizations risk significant data loss or users having unauthorized access to sensitive information.
Walter elaborated on how ransomware attacks often encrypt data already stored, and explained how proactive alerts from advanced arrays can limit damage. The array can read, encrypt, write, and proactively alert you to stop it before there is major damage.
2025 Storage Priorities
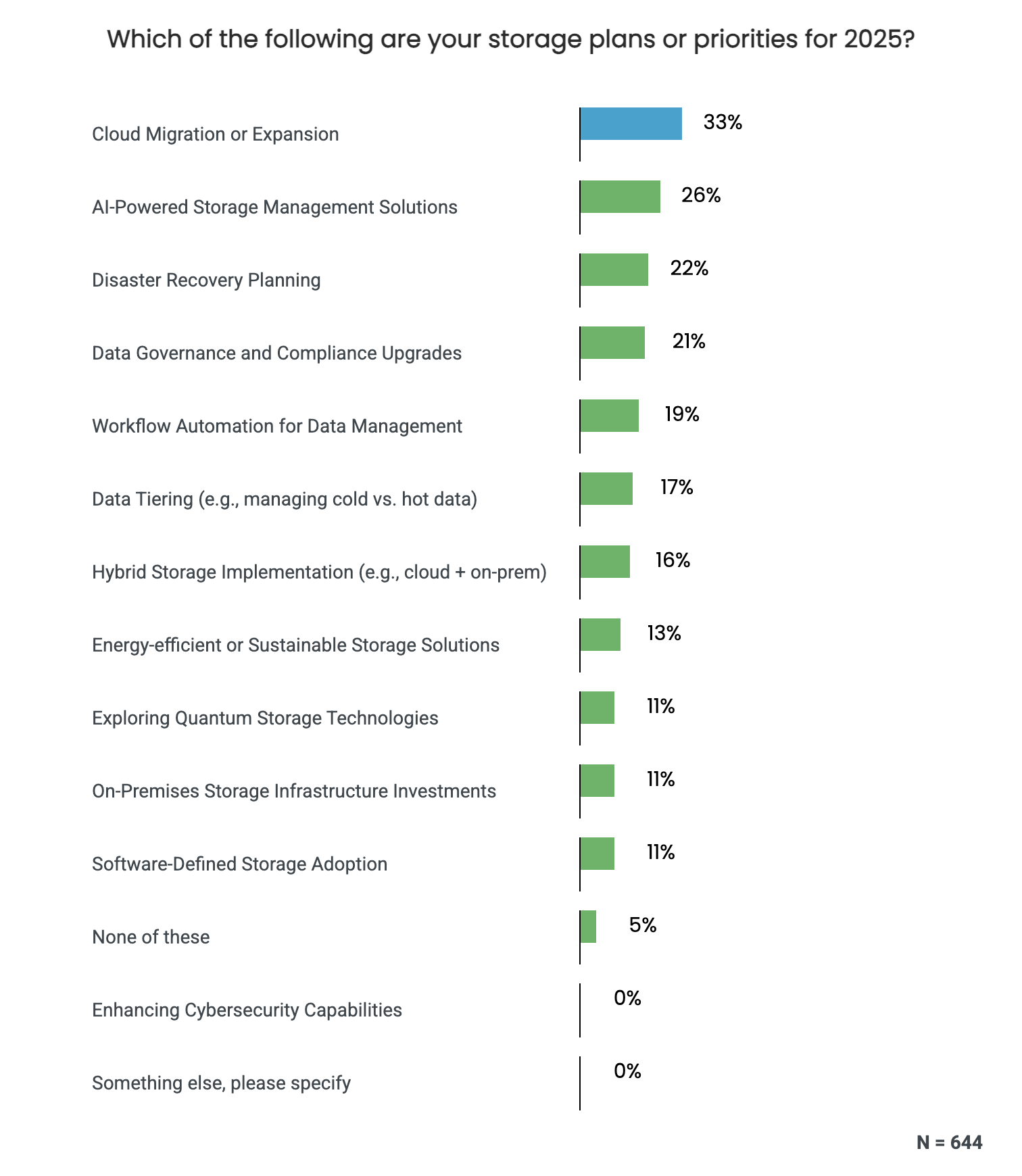
In 2025, organizations plan to invest in cloud migration or expansion (33%), AI-powered storage management (26%), and disaster recovery planning (22%).
Walter warned that traditional backup methods are often not fast enough to prevent massive data loss. Even aggressive snapshot schedules leave exposure. He stated that in one hour, an attacker can grab 100 terabytes of data. Even a one-minute delay can cost you almost two terabytes. In a second, they are taking 128 gigabytes.
He praised IBM FlashSystem for its inline corruption detection, which integrates with existing security systems and provides sub-second alerts. He mentioned that organizations get alerted to what files have been compromised and prevent significant data theft. It allows businesses to remediate and restore those files without affecting the rest of the organization, which keeps your business up and running.
Best Practices You Can Implement Today
Dean recommended following the 3-2-1 rule:
- Three copies of your data—one on primary
- Two backups of two different media types
- One copy stored offsite
He also advised creating air-gapped backups, testing backups regularly, and prioritizing mission-critical data for more frequent protection. One of his clients avoided a $3 million ransom by identifying the compromised data as non-essential thanks to strong classification protocols.
The Verdict: Hybrid & Real-Time Protection Is the Future
Most organizations today are adopting a hybrid model that blends cloud and on-premises storage. The right approach depends on factors like company size, maturity, and strategic goals. Many businesses begin in the cloud for convenience and scalability, then shift to an on-prem or hybrid setup as they grow.
On-prem storage offers greater control, simpler compliance, and clearer visibility into where data is housed. In contrast, cloud solutions provide flexibility, but can make it harder to monitor data movement and meet compliance standards. As a result, many companies now keep their most critical, high-sensitivity data on-prem, while moving less sensitive workloads to the cloud.
No matter the model, one truth remains: no organization is immune to a breach. That’s why AI-driven detection and real-time monitoring are no longer optional—they’re essential to maintaining both security and usability. As Dean emphasized, almost every quarter, another large company is in the headlines for a data breach. Having a robust architecture is extremely important.
Watch the full replay and explore more upcoming events, past sessions, and blogs for additional insights!



 Join Our Insight Gift Network
Join Our Insight Gift Network